Cracking Windows passwords with MobiusFT and JTR
This tutorial explains how to crack Windows passwords stored in the Windows Registry using the Mobius Forensic Toolkit and the John the Ripper cracker. The techniques shown here shall only be used for forensic purposes.
First, open an existing case or create a new case, as described in the Mobius Forensic Toolkit Tutorial (shipped inside the Mobius Forensic Toolkit installation package). After you have added and set up a disk into the case, open the Hive Extension view. If the Hive Extension had not run yet for this case item, it will run and will retrieve the registry files from the disk, storing them locally and building one or more registry objects.
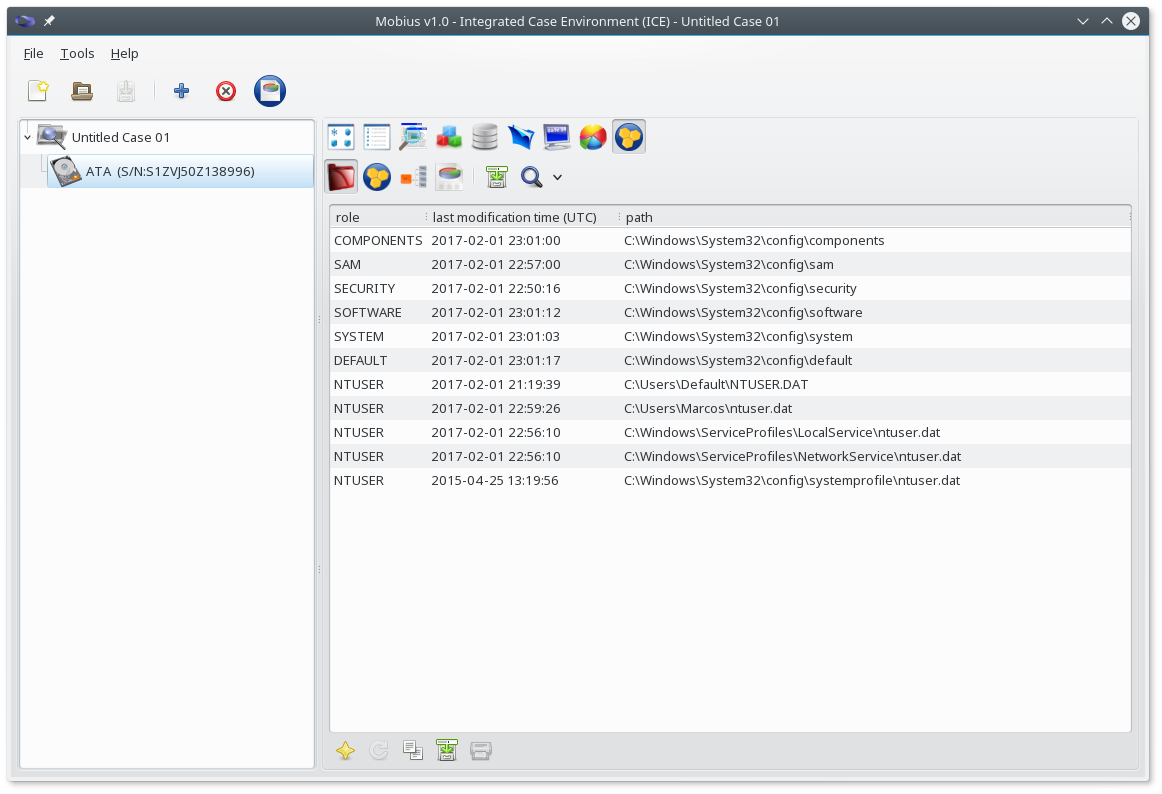
The first time a registry object is retrieved from the disk, the Hive-Turing extension is automatically run. This extension scans the registry for password artifacts, including the hashes of the user passwords, as well as passwords and candidate words such as e-mail passwords, Internet Explorer AutoComplete words and LSA secrets.
Now, open the Turing extension (main menu, option Tools→Turing). You will see a window like to one shown in the figure below, displaying password hashes, passwords and their status. As you can see, some passwords were automatically cracked, using keywords from the registry.
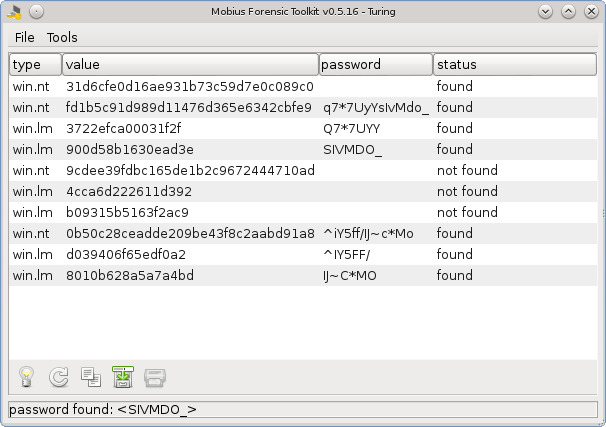
In this example, there were still 3 passwords that have not been found. So we will export the associate hashes to a John The Ripper (JTR) hashfile (*.john), using the Turing's menu option File→Export. John the Ripper is a great password cracker that can be found at http://www.openwall.com/john. Follow the instructions presented in the JTR site on how to crack those hashes. Once you have the passwords, use the menu option Tools→test dictionary, importing the .pot file generated by JTR, and the remaining passwords will be shown, like in the figure below.
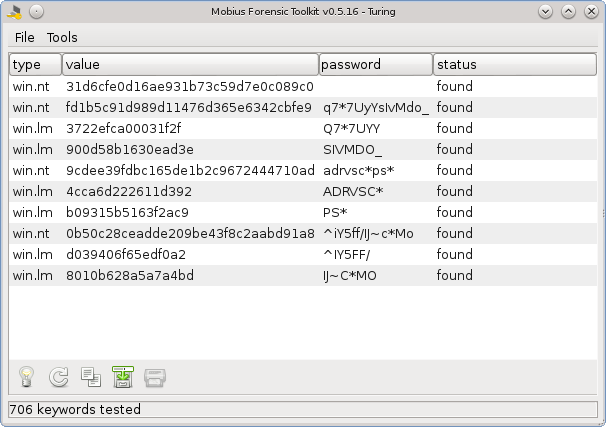
The Turing extension stores all the hashes and passwords that it finds in a database, so the next time that one of those hashes appears, the password will be automatically and instantly shown.
One last hint: When cracking Windows passwords with the JTR, try to crack first the LM hashes (when available), because they are very much easier to crack than the NT hashes. The Turing extension automatically generates the NT hash password once it has the two associated LM broken hashes.